Zygma is active in the standards development arena. Our CEO made early contribution to the development of BS 7799, antecedent of today's and ISO/IEC 27002 (i.e. the information security management standards), and is today a leading contributor to the continued development of the '27xxx family' of standards. He has also been a significant contributor to standardization development in Europe, where he worked on standards related to the European electronic signature directive.
Zygma can assist its clients compliance with regulations, legislation, imposed policies and their conformity to a range of standards. Although our experience and approach allows us to analyze any regulation or standard, those which are the more common-place are listed below.
If you have needs in other areas don't hesitate to call - we have a demonstrated and towards mapping your standards into an ISMS context, or we can do the same in an ITSM context.
We can also apply our Advanced Internal Control System () to your need to demonstrate compliance and conformity with other regulation, policy and standards.
and let us respond to your requirements with a management framework which suits your business needs.
The more common regulation and standards for which we can provide support are these:
Information Security Management
We are specialists in the building, operation and auditing of ISMSs which follow (and therefore 27002) and can also provide training (both classroom and on-the-job) and a skeleton ISMS. Zygma's approach lets its clients get on the fast track towards certification. Some will place great emphasis on ISO/IEC 27002 when talking about ISMS, but this is to miss the point: 27002 provides
only guidance (albeit valuable, well-prepared guidance which reflects best practice) - 27001 provides the definitive requirements for implementing, operating and continually improving an ISMS, including a statement of applicability which says how each of the reference controls in its Annex A (for which 27002 provides implementation guidance) apply to the ISMS in question. See other pages within our web site, such as and .
Back to Top»»
IT Service Management
Increasingly, requirements for oversight and information security are causing senior management to look at their provision of business functions in terms of services, whether their user community be internal to the organization or external to it. provides a set of requirements (in part 1) and guidance (part 2) which govern how a certifiable IT service management system should be implemented. Again based on our skeleton, we can provide the back-bone of an ITSM strategy and help clients build into that all the compliance and standards conformity requirements they have. Many of those specific needs may include one or more of the other standards we here mention. Zygma's approach lets its clients get on the fast track towards certification.
Back to Top»»
Federal Information Security Management Act
The places requirements for information security management upon the heads of all Federal agencies and is supported by a range of standards
and agency guidelines. Zygma can assist agencies in constructing their information security management systems for specific systems. We are undertaking pioneering work with the Federal PKI Authority to construct an ISO/IEC
27001-conformant ISMS which embraces all the applicable FISMA requirements and supports the C&A process. This includes compliance mapping with such major FISMA supports as NIST SP 800-53 (Revision 1).
In 2008, under GSA funding, Zygma produced a detailed mapping of IS27001:2005 (requirements and controls), prepared as a potential Annex for SP 800-63 Rev2, which can be found .
It provided a comprehensive mapping of not just the IS27001 Annex A controls against SP 800-53 but also aligned the requirements of IS27001 (i.e. clauses §4 to §8 inclusive) to controls in '-53 which were more akin to 'measures'.
For some reason NIST chose not to accept this work and to this day continues to map only to the Annex A controls, ignoring the alignment to IS27001's ISMS requirements.
Back to Top»»
FIPS 201
Zygma has produced assessment criteria for the Federal government (see our page for details) and is highly conversant with the needs upon Federal departments, agencies and industry partners in the development and operation of a PIV system. We can help clients establish their conformity and can provide independent audit of their systems. We can also build an which will support and demonstrate the organization's FIPS 201 compliance.
Back to Top»»
Sarbanes-Oxley Act
The requirements of , that public companies assess and publicly disclose the effectiveness of their internal controls as they relate to financial reporting and have those controls independently audited, have a direct relationship to information security management. Virtually no business of any magnitude today operates without a high degree of dependence on IT systems, and hence the need for effective information security management in the SOX context is paramount. We can help clients establish their SOX compliance through their ISMS, efficiently and effectively.
Back to Top»»
Gramm-Leach-Bliley Act
The imposes requirements on financial institutions to specify and implement an information security plan and to protect personal identifiable information (under its Safeguards Rule) and also to establish a published consumer privacy policy, giving the consumer the choice of opting in or out of certain provisions regarding information sharing. The Act makes no suggestion as to how the information security plan should be realized: Zygma's view is that by adopting a recognized standard which embodies best practices an institution gives itself the best defense against any challenge to its GLBA compliance. We can help you build and operate an ISMS which satisfies that need.
Back to Top»»
Federal Financial Institutions Examination Council
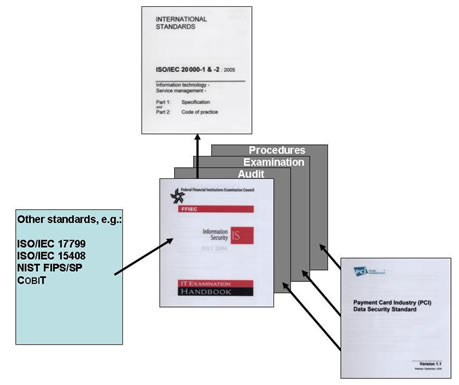
The FFIEC published its Information Security Booklet to supplement compliance with GLBA Section 501(b) guidelines. This booklet in turn refers to other standards which are recognized as being key contributors to a comprehensive management framework. Zygma's approach is to use either or as the management framework for defining how financial institutions can capture their information security management strategy and practice and apply the FFIEC guidelines in such a context. The choice of ISMS or ITSM for the management system is the client's, although we would observe that the two are not mutually exclusive: an ITSM can embrace ISMS solutions and deliver broader assurance to the users of the services in question.
The following figure illustrates this approach: